3 min read
MIPI CSI-2 Security Forum Kicks Off 2023 Education Program
![]() Ian Smith, MIPI Alliance Technical Content Consultant
:
15 February 2023
Ian Smith, MIPI Alliance Technical Content Consultant
:
15 February 2023

- News & Events
- News
- Blog
At MIPI’s first event of 2023, the co-chairs of the MIPI Security Working Group, Philip Hawkes and Rick Wietfeldt, provided a comprehensive introduction to the upcoming MIPI Security Framework, including an overview of specifications slated to be released this year, the framework’s security objectives and its underlying components.
The suite of four specifications that make up the framework is initially targeted at automotive advanced driver-assistance systems (ADAS) and autonomous driving systems (ADS) applications that require end-to-end protection of data streams between MIPI CSI-2®-based sensors and their related electronic control units (ECUs). In the near future, the same underlying security framework is expected to be applied to other application areas, such as the MIPI DSI-2℠ display protocol.
The following security-related specifications are currently being finalized, with MIPI member review scheduled in the coming months:
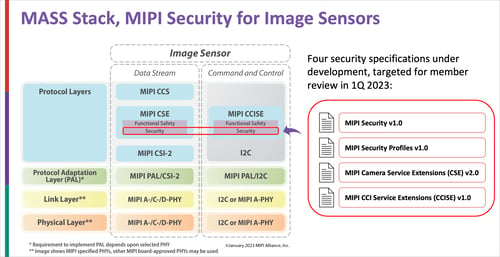
- MIPI Security℠ v1.0 provides the baseline specification which defines a system security management suite (based on the DMTF SPDM standard) to authenticate and establish secure sessions between system components and manage security services.
- MIPI Security Profiles℠ v1.0 defines a set of common security profiles to enable interoperability involving the SPDM specification.
- MIPI Camera Service Extensions (MIPI CSE℠) v2.0 includes security service extensions to apply data integrity protection and optional encryption to CSI-2 data.
- MIPI Command and Control Interface Service Extensions (MIPI CCISE℠) v1.0 includes security service extensions to apply data integrity protection and optional encryption to the MIPI camera control interface (CCI) based on I2C.
Flexibility for Achieving Security Objectives
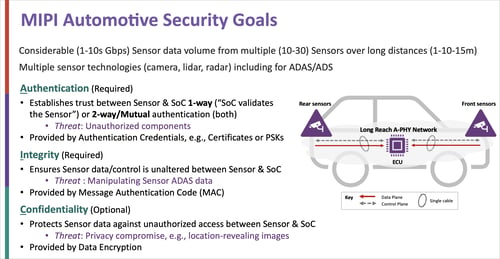
Safety-critical automotive use cases demand end-to-end protection (from pixel data source to data sink) of CSI-2 image sensor data. The MIPI Security Framework addresses this need by leveraging authentication to protect against unauthorized system components, integrity protection to prevent manipulation of sensor data and confidentiality to protect data privacy.
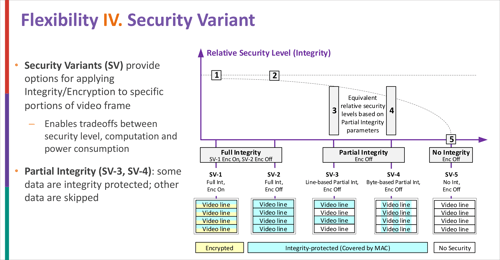
The flexible framework balances security requirements against the practical need to develop system components within tight power, size and heat tolerances. A key attribute to achieve this flexibility is the framework’s ability to support source-selective security, which enables a developer to flex the level of security to the structure of the CSI-2 protocol and, more specifically, to the anatomy of the CSI-2 image frame itself.
Furthermore, four security vectors have been built into the MIPI Security Framework to give developers flexibility in implementation:
- A choice of two security protocols (FSED and SEP), one that adds security extensions to each CSI-2 message in a frame (SEP), and one that introduces additional CSI-2 security messages into the frame (FSED)
- A choice of two cybersecurity algorithms, one for performance and another for efficiency
- A choice of six tag modes with different definitions of how often to compute message authentication codes (MACs)
- A choice of five security variants enabling different security levels, including the ability to implement partial integrity using different stride patterns applied to image data
The framework can maintain end-to-end security over a wide range of network topologies (e.g., for networks that leverage bridges, aggregators, etc.). When both security and functional safety service extensions are enabled, security is layered on top of functional safety—from a source (or transmitter) perspective, security is applied to the image data first, followed by the application of functional safety.
The Framework’s Underlying Components
The functionality of the MIPI Security Framework is based on several key components.
The system security management suite is used to authenticate components within the system, to establish secure transport channels using session keys and, using these secure channels, to read/write security context parameters within the system.
The data service protocols then synchronize and execute security contexts. In this way, the data service protocols—namely the Service Extensions Packet (SEP) and Frame-Based Service Extensions Data (FSED) protocols—enable integrity protection and optional data encryption of CSI-2 data streams.
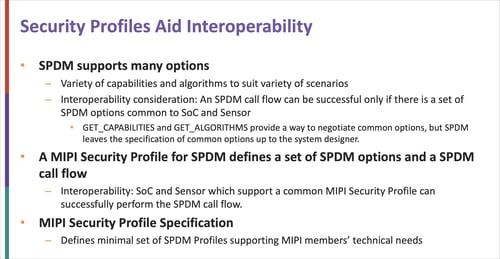
The system security management suite is built on the DMTF’s SPDM standard. Use of the SPDM protocol (which is itself based on TLS) was selected by the MIPI Security Working Group as a basis for the framework due to its flexibility and efficiency, having already been used to secure other applications that present many similarities to automotive network architectures.
The MIPI Security Profiles specification narrows down the options provided by the SPDM protocol and defines a set of common profiles to aid interoperability between system components and reduce test effort.
Find Out More
The session recording and presentation materials from the 2023 MIPI CSI-2 Security Forum are now available on demand. Additional information can be found on the Security Framework page of the MIPI website.
For updates on MIPI security specifications, upcoming events and new security resources, sign up for the security mailing list to receive notifications.