5 min read
MIPI Security Investigation Group – A Conversation with Philip Hawkes and Rick Wietfeldt
![]() Sharmion Kerley, MIPI Director of Marketing and Membership
:
11 March 2021
Sharmion Kerley, MIPI Director of Marketing and Membership
:
11 March 2021

- News & Events
- News
- Blog
Formed in 2019, the MIPI Security Investigation Group (Security IG) was established to provide recommendations for a scalable, uniform MIPI security framework and ongoing support model, as well as to offer guidance to MIPI working groups on overarching security requirements, guiding principles and policies, and external threats.
Recently the group achieved a significant milestone in evaluating approaches to secure systems-on-chips (SoCs) in automotive electronic control units (ECUs) to peripherals such as cameras, sensors and displays in support of MIPI’s automotive work. As part of this effort, the Security IG conducted a technical and strategic evaluation of DMTF’s Security Protocol and Data Model (SPDM) architecture, which provides message exchange, sequence diagrams, message formats and other relevant semantics for authentication, firmware measurement and certificate management. The evaluation confirmed that the SPDM architecture meets MIPI’s requirements for this use case. We sat down with Philip Hawkes and Rick Wietfeldt, co-chairs of the Security IG, to learn more.
Q: Tell us about the goals of the MIPI Security Investigation Group and the group’s recent milestone.
Rick Wietfeldt: The goal of the Security IG is to develop a holistic and consistent approach to ever-growing security concerns in a variety of application spaces. To do this, the group is looking at how to map industry security protocols and data models to MIPI interfaces. For instance, the primary use case that the Security IG has been focusing on in recent months is automated driving. You have camera sensors around a car, and they need to be routed or transmitted to a controller that enables autonomous driving. And the concern, of course, is safety—you don’t want an attacker coming in and modifying the pixels so that the ECU does the wrong thing.
Philip Hawkes: The Security IG has spent a lot of time understanding the details of how different components of the automotive SerDes system work together. The various components work slightly differently, and so we’ve been focused on identifying a solution that can be integrated across the entire system.
To do this, our approach is to have one main security configuration protocol that can set up secure channels between various components in the system. And we determined that DMTF’s SPDM architecture meets MIPI’s technical requirements for provisioning security configurations. That’s the evaluation that we’ve gone through: Does SPDM support the sort of authentication that we want? Is it flexible enough for us to provision security configurations for other protocols? Our evaluation process concluded that we should go forward with developing an SPDM-based solution. The Security IG is also evaluating use of related DMTF specifications.
Q: How would you describe the SPDM-based solution, and why does the group recommend it as a solution?
Rick Wietfeldt: The SPDM architecture defines a method by which a system controller, known as a “requester,” sends security-related commands to other system components, known as “responders.” Requesters can either obtain information from or send information to responders.
Philip Hawkes: The main feature that we’re exploring in SPDM is that ability to establish a secure, authenticated channel, and this approach would allow us to set up a channel between a central controller entity that’s provisioning security configurations to various target components across a system. SPDM also includes a variety of options for authentication. For example, with this approach, you have the flexibility to use certificates or shared keys—in cryptography, they are sometimes called “symmetric” or “pre-shared” keys. So rather than having a certificate infrastructure, designers could use something simpler that doesn’t require verification of a chain of certificates. The point is that there’s a variety of authentication mechanisms that DMTF supports, and they align with the options in which MIPI members have expressed interest.
Q: Security is an important component of the MIPI Automotive SerDes Solutions (MASS). How does this effort fit into MIPI’s automotive development efforts?
Rick Wietfeldt: MASS is an end-to-end, full stack of connectivity solutions supporting automated driving, advanced-driver assistance systems (ADAS) and other automotive applications. MASS helps automakers integrate new and emerging safety features such as low-latency backup cameras, lane-keeping and sign-detection sensors, and 360-degree camera, lidar and radar systems, as well as high-resolution instrumentation, control and entertainment displays.
So, within this system, the three data protection services that MIPI covers are high-bandwidth digital content protection (HDCP), functional safety (FuSa) and then, very broadly, security. HDCP is used primarily to secure premium content such as Hollywood movies, while FuSa provides data protection against non-intentional errors, and security protects against the injection of intentional errors or eavesdropping by bad actors. Using all three approaches as needed, MIPI Alliance is defining an end-to-end system for data protection that can be enabled either from bridge to bridge or across the entire stream from source to destination.
Philip Hawkes: As part of MASS, the forthcoming MIPI Camera Service Extensions (CSE) and Display Service Extensions (DSE) specifications will deliver the FuSa data protection capabilities, as well as the HDCP required for display applications. (These specifications are scheduled for release in the coming months.)
Plans call for security—including authentication, privacy (encryption), message integrity and replay protection—to be introduced later this year, through a new security-specific specification(s), and updates to the CSE and DSE specifications.
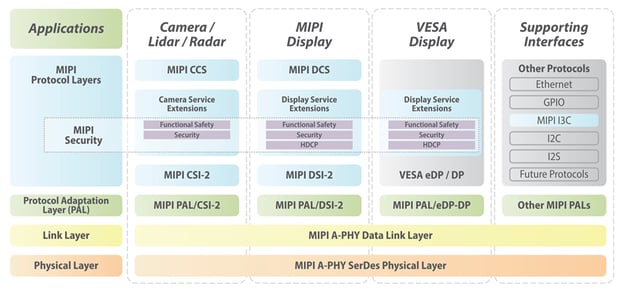
MIPI security framework applied to MIPI Automotive SerDes Solutions (MASS)
Q: What collaboration is taking place within the MIPI working groups to develop the security framework and related specifications?
Rick Wietfeldt: The work of the Security IG has been designed from the outset to align architecturally with other MIPI working groups who are seeking security solutions. The Security IG serves as a forum for broader security discussions among MIPI working groups, as well as to streamline efforts and promote consistent approaches across our protocols. That said, to date, we’ve worked most closely with the MIPI Camera, MIPI Display and MIPI Debug working groups, and have had early discussions with the MIPI I3C Working Group.
Q: What’s the roadmap for the Security IG in 2021 and beyond?
Philip Hawkes: The Security IG expects to evolve into an official MIPI working group in the near future to begin the specification development process. Our work started in 2016 with the formation of a security BoF (Birds of a Feather) group, and that effort migrated into an investigation group in 2019. We’ll continue to evolve as a group as our work matures.
Q: What resources exist, and how can security experts become involved?
Rick Wietfeldt: You can learn more about MIPI Alliance’s work in the automotive space, as well as the MIPI Security IG and MIPI Camera, MIPI Debug, MIPI Display and MIPI I3C working groups. Further, the SPDM architecture and related specifications continue to be actively developed within the Platform Management Communications Infrastructure working group of DMTF, as well. The Security IG is also evaluating use of these related DMTF specifications. It’s important to note that we are introducing broad and advanced security aspects across many popular protocols and wired connectivity interfaces for the first time, often replacing existing proprietary and less-sophisticated solutions, so this initiative will necessitate broad industry discussion and exploration.
Philip Hawkes: We’d encourage security experts, particularly those working in automotive, to engage with MIPI Alliance. This is also where we see that MIPI’s liaison relationships with organizations such as DMTF and JasPar (Japan Automotive Software Platform and Architecture) are so critical. We welcome further inputs from those in this field, especially from original equipment manufacturers (OEMs), Tier 1 suppliers, and other designers and implementers of automotive systems.
Philip Hawkes, Ph.D., is principal engineer of technology at Qualcomm Technologies Inc. Philip primarily works on security aspects in standards organizations. He is the co-chair of the MIPI Security Investigation Group.
Rick Wietfeldt, Ph.D., is senior director of technology at Qualcomm Technologies Inc. He is a director on the MIPI Alliance board of directors, as well as co-chair of the MIPI Security Investigation Group.